Electronic Voting Security
Security Definitions and Recommendations for Your Event
COVID-19 National Emergency and Public Health Emergency has been cancelled on May 11, 2023.
Meridia still recommends that you use Visual Vote Confirmation as a best practice in secure electronic voting.
Thank you for working with us so diligently over the last three years to make things work even in the most difficult of environments.
High Standard of Electronic Voting Security
Each Meridia electronic voting system comes with these standard security features:
Increase Voting Security at Your Event
Control the Audience
Your are in control of who gets the clicker to vote with. Only a registered voter should be given one at the registration desk.
Verify their identity with Drivers License scanner, or a voter registration spreadsheet.

Control the Voting Area
Set up Perimeter Security
Define the ‘voting area’ where the registered voters can congregate and expect the system to work reliably.
Enforce the rules on giving up a keypad when leaving the designated area and picking it up when they return.
Be aware that all Meridia products are designed to work together.
Participants in possession of unauthorized Meridia devices and/or malicious lookalikes can interfere with your system.
Disable Lost and/or Rogue Keypads
Easily Disable Clickers Out of Your Control
There’s no way you can prevent all theft, but when it happens, you can easily disable the keypads you no longer have control over.
Set up a Participant List (even if it’s anonymous – without names associated with the clickers) and remove the devices that are not in the distribution bags.
Watch for Malicious Intent
Secure the Vote
Meridia system is protected from all external, internet-based attacks as it is an offline, closed-circuit, short-range voting system.
The only threat are the people in the vicinity of the voting system. Make sure that Meridia equipment is physically protected from accidental and/or intentional mishandling, such as disconnecting the base receiver, disabling or otherwise manipulating the voting clickers, or accessing the voting computer and software.
Use a dedicated, secured laptop and create secure protocols to handle the custody of the keypads. They are, in essence, the people’s ballots, so treat them with the same level of responsibility.
Any voting system can be overwhelmed by a ‘jammer’ if it is powerful enough and close enough.
Make sure you walk the perimeter of the designated voting area and look for persons of interest or devices that may be trying to disrupt your business.

Create a Closed System
Configure the Keypads to Only Work with Specific Receiver
You can control which specific keypads work with your base receiver. Only those keypads you program to work with “Base A” will then be able to communicate with it, leaving any other keypads (lost or stolen) ‘dead in the water’
Explain the Voting System Security
Making Everyone Trust the System is Paramount
Without trust in the system, there is little chance that your voters will be comfortable using it.
Explain how to use it (download our instruction slides and customize them if needed) and prove to them that their votes are counted.
Use a Voting Grid option in the TownVOTE software for a test question/vote to show that each voter box ‘lights up’ when they push their button.
The video on the right shows how a voter receives a ‘vote confirmation message’ (OK) after each vote – even when they need to correct their first entry.
No Internet Connectivity Required
Stay Offline. Stay Safe.
For security purposes, the voting system is completely isolated from the internet. We recommend that you put your dedicated ‘voting computer’ in Airplane Mode, which turns off all radios – Bluetooth and Wi-Fi included.
After the voting software has been installed and activated (the one time you’ll need internet), it operates locally on a closed RF network.
We maintain security via multiple layers of assurances. See our Wireless Protocol Security Statement – the RF communication protocol is close-ended, proprietary, and secured by multiple layers of data checks.
The base receiver (antenna) is a memory-less USB ‘stick’ that cannot store any data, thus it cannot be used to upload any malicious code to your computer/network.
All your voting session data remains stored on your local hard drive.
Can Another RF System Interfere with Voting?
Yes, In Theory. But It’s Harder Than That.
In theory, any ‘Free Match’ Meridia system can interfere with another ‘Free Match’ Meridia system if they operate within range of each other at the same time. To prevent interference, we can program the keypads for you in ‘Fixed Match’ mode, so that Base A only works with keypads from Group A and Group B keypads will only work with Base B and will not interfere with Group A or Base A.
Free Match mode means that any keypad will work with any base receiver. This allows for easy replacement, borrowing keypads, or splitting a system into two independent ones (with an extra receiver) when using them in separate locations.
Fixed Match is necessary when two or more systems are expected to operate within each other’s communications range. In Fixed Match mode, each receiver is ‘matched’ or ‘paired’ with a specific number of keypads and only those will work in the vicinity of the receiver.
Other RF devices can cause ‘interference‘ or ‘jamming‘ of the Meridia system. If it is a non-malicious interference, you don’t have to worry about it – our system will find a way around it on about eighty different channels and deliver the votes, albeit it might be slower than usual.
But if the interference is malicious, you have a situation that needs your full attention. First, try to detect where the attack is coming from. Being a closed-circuit system and disconnected from the internet, you can only be attacked in or near your voting area.
Second, a suspicious device or individual will have a computer system (hardware) that is being used at the same time when your vote is open and will most likely have one or more antennas connected to the computer.
Only an individual who is in possession of a Meridia system, reverse-engineered (makeshift device), or other malicious tools in the vicinity of your voting area can interfere, or completely block (jam) your voting process.
In other words, if you keep your voting area safe, your voting process is safe as well.
How Would I Know That I'm Being Attacked?
The Vote Count, or Vote Values Don’t Match Expectations
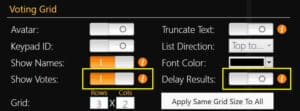
Meridia has the only voting system with Visual Vote Confirmation (Voting Grid) that can detect malicious activity in real time and visually confirm that the votes received are correct.
If you are suspicious that someone is trying to manipulate your votes, simply switch to the Voting Grid (Participant Grid) mode in TownVOTE and allow the vote value be visible in real time. To do this, turn Show Votes ON, and Delay Results OFF:
What Else Can Go Wrong?
Not Much of You Haven’t Seen Before
You should always be aware of bad actors. They could be just disruptors. They could be looking to access your dedicated voting computer. Someone may ‘accidentally’ disconnect your receiver or bring/steal keypads from the voting area.
If you have any questions, or concerns, feel free to contact us at support@meridiaars.com or 610-260-6800 x 2 (Support).
